Make Identity Risk Visible and Actionable
Whether it’s IAM, PAM, or IGA – none of it works without identity intelligence.
SPHERE provides a real-time lens into every identity and entitlement across the stack, exposing hidden risks and enabling control.
Eliminate Blind Spots Before
Attackers Exploit Them
Most organizations can’t answer who has access to what.
SPHERE delivers continuous visibility into accounts, permissions, and misaligned access across AD, PAM, and data.
Resolve Accountability,
Unlock Remediation
Without clear ownership, remediation efforts stall and risk compounds.
SPHERE maps every identity to a responsible owner so decisions can be made, and action taken, without delay.
Replace Manual Cleanup
with Automated Control
Identity threats move fast. Manual processes don’t.
SPHERE automates remediation and enforcement so high-risk access is removed before it leads to a breach.
Trusted By:
The Threats are Real
Identity is the new attack surface. Excessive access, orphaned accounts, and unowned credentials are top breach enablers – and most environments are full of them.
Meanwhile, auditors, insurers, and regulators now expect continuous control (not just one-time cleanup).
of breaches involve compromised privileged credentials
is the average cost of a breach
that’s how often a cyber attack occurs
Catch the Risk Before the Breach
Intelligent Discovery
See identity anomalies before attackers do.

Analytics & Ownership Controls
See identity risks before attackers do.

Automated Remediation
Fix what’s broken, before it spirals.
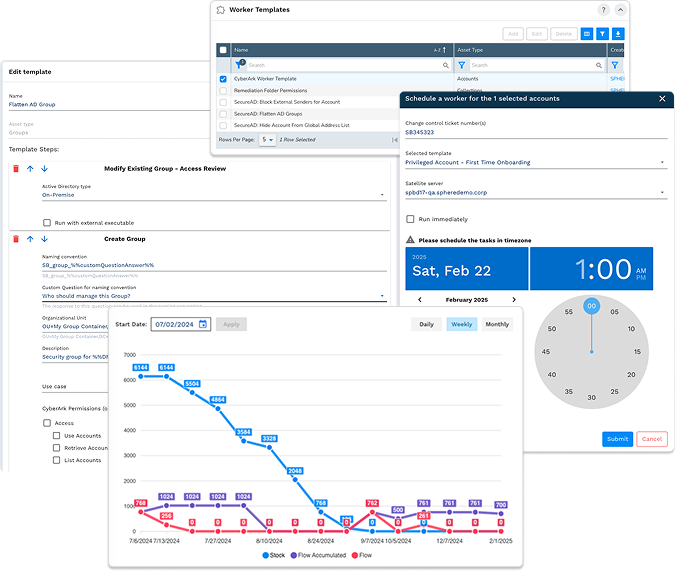
Attack Surface Reduction Made Easy
Home-grown solutions are cumbersome and hard to maintain. New vendors have gaps. SPHERE is the most established and battle-tested operator in the space.
IN DAYS
Expose what’s been overlooked
In days, you will begin to identify new accounts you previously didn’t even know existed.
IN WEEKS
Prioritize and act
Identify and remediate the riskiest issues first – reducing exposure quickly without waiting for a full-scale rollout.
IN MONTHS
Stay ahead of threats
Shift from reactive cleanup to continuous control with monitoring, ownership validation, and automated remediation.
Hear from Our Customers
![]()
How JetBlue Enhanced Their Cybersecurity Posture by Using SPHEREboard
JetBlue, a pioneer in aviation technology, partnered with SPHERE to overcome key challenges in Active Directory (AD) hygiene, privileged access, and User Access Recertifications (UARs). SPHEREboard helped streamline access management, retire outdated groups/accounts, and boost operational efficiency, resulting in faster reviews, improved compliance, and significant time savings.





