Executive Summary
Zero Trust has evolved from buzzword to mandate, yet 87% + of organizations still experienced multiple identity-related breaches last year despite having Zero Trust initiatives in place. The disconnect? Traditional Zero Trust implementations focus on network perimeters and authentication layers while missing the fundamental challenge: you can’t verify what you can’t see, and most organizations can’t see 56% of their machine identities.
Identity Intelligence, the continuous discovery, analysis, and remediation of identity risks, has emerged as the critical missing layer in Zero Trust architectures. As Gartner recognized in their 2025 Hype Cycle with the introduction of Identity Visibility and Intelligence Platforms (IVIP), organizations need more than just authentication and authorization. They need complete visibility into every identity, continuous risk assessment, and automated remediation capabilities.
This guide examines why identity has become the primary attack vector, how Zero Trust strategies are failing without comprehensive identity intelligence, and what security leaders must do to build resilient identity security architectures that actually work.
The Identity Security Crisis: Why Zero Trust Strategies Are Failing
The Uncomfortable Truth About Identity-Based Attacks
IBM’s 2025 Cost of a Data Breach Report reveals a stark reality: organizations in the United States now face average breach costs of $10.22 million, a record high. The primary culprit? Identity-related incidents that exploit the massive blind spots in our identity infrastructure.
Consider the scope of the problem:
- Machine identities now outnumber human identities 82 to 1, with 42% possessing privileged or sensitive access
- IAM teams only control 44% of non-human identities, leaving the majority unmanaged and invisible
- Malicious insider attacks cost organizations $4.92 million on average, the highest among all attack vectors
- 97% of AI-related security breaches involved systems lacking proper access controls
The traditional Zero Trust mantra of “never trust, always verify” breaks down when organizations don’t know what identities exist, who owns them, or what they can access.
The Service Account Explosion Nobody’s Talking About
While CISOs focus on securing human identities with MFA and SSO, service accounts multiply in the shadows. These non-human identities include API keys, OAuth tokens, AI agents, and automation credentials, and have become the preferred attack vector for sophisticated threats.
Organizations typically discover they have 2-3 times more privileged accounts than employees. Even worse, 42% of organizations don’t even know how many orphaned accounts exist in their environment. Each unknown account represents a potential backdoor that bypasses every Zero Trust control you’ve implemented.
Case Study: The Real Cost of Identity Blind Spots
Recent high-profile breaches demonstrate the pattern: attackers don’t break in, they log in. Using compromised credentials, often from service accounts nobody knew existed, threat actors move laterally through environments for an average of 241 days before detection.
The emergence of AI-powered attacks compounds this risk. IBM found that 16% of breaches now involve attackers using AI, primarily for sophisticated phishing (37%) and deepfake impersonation (35%). When these AI-enhanced attacks target unmanaged service accounts, the results are catastrophic.
What is Zero Trust Identity Intelligence?
Zero Trust Identity Intelligence represents the evolution of Zero Trust architecture from network-centric to identity-centric security. It’s the practice of applying Zero Trust principles specifically to identity management through continuous discovery, verification, and risk assessment of every identity, human and machine, across your entire environment.
Unlike traditional IAM approaches that operate in silos, Zero Trust Identity Intelligence creates a unified view of identity risk, enabling organizations to:
- See every identity across AD, cloud platforms, databases, and infrastructure
- Verify ownership of every account, especially service and orphaned accounts
- Assess risk continuously based on privilege levels, access patterns, and behavioral analytics
- Remediate automatically through policy-driven workflows that don’t disrupt operations
This isn’t about replacing your existing PAM, IGA, or IAM tools. It’s about creating the connective tissue that makes them effective.
The Zero Trust Identity Intelligence Framework
Core Principle 1: Continuous Identity Discovery
The Challenge: You can’t protect what you don’t know exists. Traditional discovery methods provide point-in-time snapshots that become outdated within days.
The Solution: Continuous, automated discovery across all identity stores including Active Directory, LDAP, cloud platforms, databases, and infrastructure. This means real-time visibility into:
- Local admin accounts on Windows and UNIX systems
- Service accounts embedded in applications
- Cloud IAM roles and policies
- Database superuser accounts
- API keys and OAuth tokens
- AI agents and automation identities
Key Capability: Discovery must be agentless and non-intrusive, scanning across dozens of platforms and systems without requiring installations that could themselves become attack vectors.
Core Principle 2: Comprehensive Identity Visibility
The Challenge: Identity data exists in fragments across dozens of systems. Security teams see pieces but never the complete picture.
The Solution: A unified identity intelligence layer that correlates data from all sources, providing:
- Complete identity inventory with classification by type and risk
- Privilege mapping showing who can access what
- Entitlement chains revealing hidden access paths
- Group membership analysis exposing circular and nested permissions
- Cross-platform correlation linking identities across systems
Key Capability: The platform must integrate with existing tools (PAM, IGA, SIEM) to enrich their data rather than creating another silo.
Core Principle 3: Automated Identity Hygiene
The Challenge: Manual identity cleanup is impossible at scale. By the time you’ve reviewed 10,000 accounts, another 1,000 have been created.
The Solution: Policy-driven automation that continuously:
- Removes stale and orphaned accounts
- Rotates credentials on schedule
- Enforces least privilege by removing excessive permissions
- Onboards high-risk accounts to PAM systems
- Resolves group membership issues
- Updates ownership mappings
Key Capability: Automation must include safeguards to prevent business disruption, with impact modeling before any remediation action.
Core Principle 4: Risk-Based Identity Governance
The Challenge: Not all identities carry equal risk, but most organizations treat them the same.
The Solution: Dynamic risk scoring that considers:
- Privilege levels and scope of access
- Account usage patterns and anomalies
- Ownership status and validation
- Compliance with security policies
- Blast radius of potential compromise
- Integration with threat intelligence
Key Capability: Risk assessment must be continuous and contextual, adapting as the environment changes.
Visual Framework: The IVIP Integration Architecture
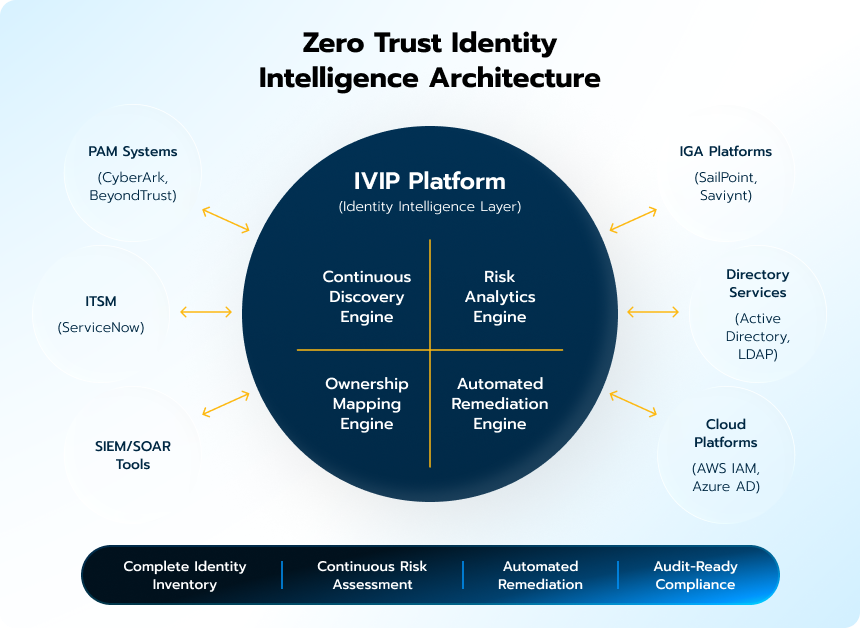
Center Hub: IVIP Platform (Identity Intelligence Layer)
- Continuous Discovery Engine
- Risk Analytics Engine
- Ownership Mapping Engine
- Automated Remediation Engine
Surrounding Spokes (Existing Tools):
- PAM Systems (CyberArk, BeyondTrust)
- IGA Platforms (SailPoint, Saviynt)
- Directory Services (Active Directory, LDAP)
- Cloud Platforms (AWS IAM, Azure AD)
- SIEM/SOAR Tools
- ITSM (ServiceNow)
Data Flows:
- Bidirectional arrows showing data enrichment
- Discovery feeds from all sources to IVIP
- Risk intelligence flowing back to tools
- Automated workflows triggering remediation
Key Outcomes (Bottom Layer):
- Complete Identity Inventory
- Continuous Risk Assessment
- Automated Remediation
- Audit-Ready Compliance
Measuring Success: KPIs for Zero Trust Identity Intelligence
Identity Hygiene Score
Track the percentage of identities that meet your security standards:
- Owned: Has an assigned, validated human owner
- Classified: Properly categorized by type and risk level
- Protected: Appropriate controls based on privilege level
- Compliant: Meets regulatory and policy requirements
Target: Continuous improvement in identity hygiene score with regular milestone reviews
Mean Time to Remediation (MTTR)
Measure how quickly identity risks are addressed:
- Discovery to ownership assignment: Target < 24 hours
- Risk identification to remediation: Target < 72 hours
- Policy violation to correction: Target < 48 hours
Organizations using IVIP with extensive automation achieve identification and containment times that are 80 days faster than those using manual processes, according to IBM’s research on security AI and automation.
Privileged Account Exposure Reduction
Track the decrease in unprotected privileged accounts:
- Unvaulted privileged accounts: Target significant reduction in first 90 days
- Orphaned privileged accounts: Eliminate systematically over 6 months
- Over-privileged service accounts: Reduce through continuous least privilege enforcement
MetLife achieved 18-platform visibility and eliminated manual certifications entirely using this approach.
Automated Remediation Percentage
Measure the shift from manual to automated identity management:
- Account onboarding to PAM: Target high automation rates
- Stale account removal: Implement policy-based automation
- Group membership cleanup: Automate based on business rules
- Ownership updates: Streamline through workflow automation
Citizens Bank achieved complete automation across their CyberArk, SailPoint, and ServiceNow integrations.
Technology Requirements and the IVIP Advantage
Essential Capabilities for Zero Trust Identity Platforms
Modern Zero Trust architectures require identity platforms that provide:
1. Universal Discovery
- Agentless scanning across all platform types
- Real-time detection of new identities
- Shadow IT and shadow AI discovery
- Cross-environment correlation
2. Intelligent Analytics
- Machine learning-powered risk scoring
- Behavioral baseline establishment
- Anomaly detection and alerting
- Predictive risk modeling
3. Automated Governance
- Policy-based remediation workflows
- Safe credential rotation
- Least privilege enforcement
- Continuous compliance validation
4. Seamless Integration
- Native connectors to PAM/IGA/IAM
- API-driven architecture
- ITSM workflow integration
- SIEM/SOAR data enrichment
How IVIP Addresses Each Requirement
Identity Visibility and Intelligence Platforms represent a hype cycle that will lead to a potential new category, designed specifically to provide the missing identity intelligence layer. Unlike traditional tools that operate in silos, IVIP platforms:
- Augment rather than replace existing investments in PAM, IGA, and IAM
- Provide unified visibility across all identity stores and platforms
- Enable continuous hygiene through automated discovery and remediation
- Deliver measurable risk reduction through data-driven prioritization
As Gartner notes: “Even with mature IGA, AM and PAM solutions, many organizations struggle to achieve full visibility (‘single pane of glass’) in a reasonable timeline and at sustainable cost.”
Integration With Your Existing Security Stack
IVIP platforms enhance your current tools by:
- Feeding clean identity data to PAM systems for accurate vaulting
- Enriching IGA platforms with real-time ownership and usage data
- Providing SIEM systems with identity context for better threat detection
- Enabling SOAR platforms to automate identity-based response actions
ROI Framework: Calculating Identity Intelligence Value
Calculate your potential return using this framework:
Cost Savings:
- Reduced breach risk: (Current breach probability × $10.22M) × risk reduction percentage
- Audit efficiency: Annual audit hours × hourly rate × efficiency improvement
- Manual process elimination: FTEs on identity management × salary × automation rate
Risk Reduction:
- Privileged account exposure: Number of unprotected accounts × average breach cost per account
- Compliance penalties avoided: Historical penalties × risk reduction factor
- Operational disruption prevented: Downtime costs × prevention rate
Real-world example: A healthcare enterprise identified over 75,000 accounts and achieved 60% risk reduction within a month, as documented in identity hygiene case studies. Coca-Cola FEMSA achieved centralized control and enforced least privilege across their entire environment, demonstrating clear ROI within months.
Industry-Specific Considerations for Zero Trust Identity
Financial Services: Beyond Compliance to Resilience
Financial institutions face unique identity challenges:
- Regulatory Requirements: SOX, PCI-DSS, and FFIEC mandate strict access controls
- Third-Party Access: Vendors, auditors, and partners require temporary privileged access
- Legacy Systems: Mainframes and older platforms with embedded service accounts
- Real-Time Trading: Systems that can’t tolerate any authentication latency
Zero Trust Approach: Implement continuous identity certification with automated evidence collection. Focus on service account discovery in trading systems and real-time risk scoring for privileged access.
Healthcare: Protecting Patient Data and Clinical Systems
Healthcare organizations must balance security with accessibility:
- HIPAA Compliance: Detailed access logging and regular access reviews
- Clinical Workflows: Doctors and nurses need rapid, context-aware access
- Medical Devices: IoT devices with embedded, unchangeable credentials
- Research Environments: Collaborative spaces with complex permission requirements
Zero Trust Approach: Deploy identity intelligence that understands clinical workflows. Prioritize discovery of medical device identities and implement compensating controls where credentials can’t be rotated.
Manufacturing: Securing OT and IT Convergence
Manufacturers face identity challenges across converged environments:
- Operational Technology: SCADA systems and PLCs with legacy authentication
- Supply Chain Integration: B2B connections requiring federated identity
- Shift Operations: Shared accounts used across multiple operators
- Intellectual Property: CAD systems and research platforms with sensitive data
Zero Trust Approach: Focus on discovering and mapping OT system accounts. Implement identity intelligence that can bridge IT and OT environments without disrupting production.
Cloud-Native Organizations: Managing Ephemeral Identity Scale
Born-in-the-cloud companies have different challenges:
- Ephemeral Identities: Containers and functions creating temporary credentials
- Multi-Cloud Complexity: Identities scattered across AWS, Azure, and GCP
- DevOps Velocity: Continuous deployment requiring automated access provisioning
- API Economy: Thousands of API keys and OAuth tokens
Zero Trust Approach: Implement continuous discovery that can track ephemeral identities. Focus on API key governance and automated secret rotation integrated with CI/CD pipelines.
The Path Forward: Building Your Zero Trust Identity Intelligence Program
Immediate Actions for Security Leaders
Week 1-2: Assess Current State
- Inventory existing IAM, PAM, and IGA tools
- Identify visibility gaps in identity coverage
- Document known identity-related risks
- Calculate potential breach impact
Week 3-4: Define Success Criteria
- Establish identity hygiene baselines
- Set risk reduction targets
- Define automation goals
- Create compliance requirements matrix
Month 2: Evaluate IVIP Solutions
- Assess integration capabilities with existing tools
- Validate discovery coverage across your environment
- Test automation workflows in non-production
- Calculate ROI based on your specific risks
Month 3: Build Implementation Plan
- Prioritize high-risk identity categories
- Design phased rollout approach
- Establish governance structure
- Create success metrics dashboard
Critical Success Factors
- Executive Sponsorship: Identity intelligence must be a board-level priority
- Cross-Functional Collaboration: Include IAM, PAM, GRC, and operations teams
- Continuous Improvement: Treat identity hygiene as an ongoing discipline
- Automation First: Manual processes won’t scale with identity growth
- Risk-Based Prioritization: Focus on highest-impact identities first
Frequently Asked Questions
What is Zero Trust Identity Intelligence?
Zero Trust Identity Intelligence is the practice of applying Zero Trust principles, never trust, always verify, specifically to identity management through continuous discovery, risk assessment, and automated remediation of all identities across an enterprise environment.
How does Identity Intelligence differ from traditional IAM?
Traditional IAM focuses on provisioning and authentication, while Identity Intelligence provides continuous visibility, ownership mapping, and risk assessment across all identity types. It augments IAM tools rather than replacing them.
Why can’t existing PAM/IGA tools provide identity intelligence?
PAM and IGA tools excel at policy enforcement but weren’t designed for continuous discovery across diverse platforms or for managing the explosion of machine identities. They need clean, complete identity data to function effectively.
What are machine identities and why do they matter?
Machine identities include service accounts, API keys, OAuth tokens, and AI agents. They outnumber human identities 82:1, often have privileged access, and are the primary target in modern attacks.
How quickly can organizations see results from Identity Intelligence?
Organizations typically see immediate value from discovery (days), achieve significant risk reduction within 30-60 days, and reach identity hygiene maturity within 3-6 months.
Does implementing Identity Intelligence require replacing existing tools?
No. Identity Intelligence platforms integrate with and enhance existing PAM, IGA, and IAM investments by providing the visibility and intelligence layer these tools need to be effective.
What’s the typical ROI for Identity Intelligence platforms?
Organizations report significant risk reduction, substantial audit efficiency improvements, and breach prevention value that far exceeds platform costs, especially given average breach costs of $10.22 million in the US.
How does Identity Intelligence support Zero Trust initiatives?
It provides the foundational identity visibility required for Zero Trust by ensuring you know every identity, understand its risk, and can verify it continuously. You can’t verify what you can’t see.
Deepen Your Identity Intelligence Knowledge
Essential Guides:
- Identity Intelligence: Everything You Need to Know – The complete guide to Identity Intelligence as a discipline
- IVIP: The New Gartner Category Explained – Why Gartner added IVIP to their 2025 Hype Cycle
- The Rise of Non-Human Identities – Managing the 82:1 machine-to-human identity ratio
Implementation Resources:
- SPHEREboard Platform Overview – See how IVIP creates unified identity intelligence
- SPHEREboard for CyberArk PAM – Maximize your PAM investment
Industry Research:
- Identity Hygiene in PAM and IGA Strategy – Dr. Edward Amoroso’s eBook on integration strategies
Take Action: Assess Your Identity Intelligence Maturity
The gap between Zero Trust promise and reality is identity visibility. With 87% of organizations experiencing identity-related breaches despite Zero Trust initiatives, the message is clear: you need Identity Intelligence to make Zero Trust work.
Ready to close your identity visibility gaps?
Schedule a 20-minute Identity Intelligence Assessment to:
- Discover your true identity footprint across all platforms
- Identify high-risk accounts and ownership gaps
- Receive a customized Zero Trust Identity roadmap
- See how IVIP can accelerate your Zero Trust initiative
Don’t wait for the next breach to reveal your identity blind spots. The path to effective Zero Trust starts with complete identity visibility.
Schedule your Demo | Download the Intelligent Discovery Brief
SPHERE pioneered Identity Hygiene and continues to lead the Identity Intelligence category. Our SPHEREboard platform helps organizations achieve continuous identity visibility, ownership, and control—the foundation of effective Zero Trust architecture.

