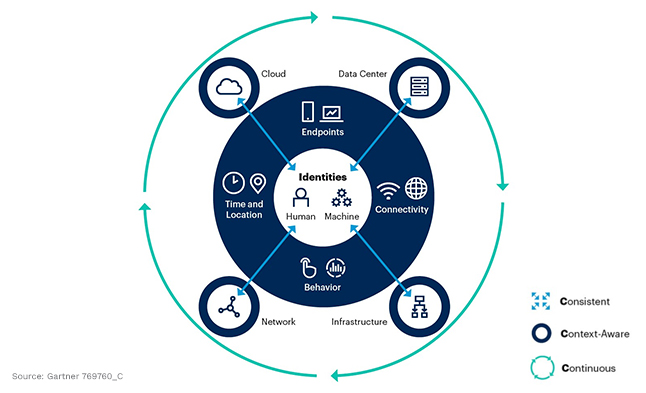
The 3 C’s in Gartner’s Identity-First Security approach state that identity security needs to be Consistent, Context-Aware, and Continuous. In this article, we will review what these concepts mean, and why they are so important to Identity-First security.
We know what the 3 C’s are, but what do they mean?
- Consistent – Something that is done regularly
- Context-Aware – How or where is an object being used?
- Continuous – Tasks that are uninterrupted, or completed all the time, unending
So, what does this mean regarding identity-first security? By now we’ve figured out that while our security perimeter extends to on-prem firewalls and cloud environments, it starts with identities. This means that if you can protect these identities and put limits around them—like removing standing access, practicing the principles of least privilege, and enforcing Just-in-Time (JIT) access—you will vastly improve your overall security posture. Undoubtedly, Identity security must come first in any established environment.
The First “C”: Consistent
The first principle in this approach is Consistent. This revolves around the practice of consistently searching for and protecting new and existing (and potentially unknown) identities. As people join, leave, or move throughout an organization, their roles change. It then stands to reason that, with those changes, the access that their identity should or shouldn’t have also will change.
Likewise, as machines and services are commissioned and decommissioned, they require a similar level of scrutiny regarding the access that they should or shouldn’t have.
With frequent changes happening to both human and non-human identities across the organization, this requires:
- Consistent awareness of what identities exist
- Consistent upkeep of those identities and;
- Consistent testing of the mechanisms, processes, and policies in place that monitor and protect our identities.
The Second “C”: Context-Aware
The next principle in this approach is Context-Aware. In the quest to find, monitor, and protect all identities within our organizations, we must understand the context of these identities. There are any number of questions that could be asked to provide this context, like:
- How are these identities being used?
- Which account types do they have access to?
- Do they need this access?
These identities can be human, or machine identities and they can exist within data center hosting platforms and appliances, infrastructure servers and storage devices, network devices like switches, routers, and firewalls, or cloud environments like Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), and more.
Other security elements that require contextual awareness include understanding what endpoints these identities should be operating from, how they normally behave, what they normally connect to or access, and the location and times of their normal operations. Each of these elements helps provide a better understanding of how an identity is being used so we can more accurately secure it. It also helps us to pinpoint anomalies, should an identity be compromised, and start to behave in a way that is outside of the norm.
The Third “C”: Continuous
The final principle that we will review is Continuous. We must practice endless consistency and contextual awareness to the point of it becoming normal and habitual in the way that we conduct identity security. You might be asking, “Well, how do I do that?”. Practically speaking, if your company is already mature enough in its identity security to practice the first two principles, congratulations! Your organization is among the few in the world to get this far. This makes explaining the third principle rather simple for you, “KEEP DOING IT.”
For the rest of us who are trying to wrap our minds around how to mechanically accomplish this daunting task, don’t worry, there IS hope. The answer is not to do this manually or to spend the time to develop your own software to accomplish this monumental task. Our ever-growing cybersecurity industry has provided plenty of viable tooling options already on the market to help you accomplish this undertaking.
How SPHERE Leverages the 3 C’s Approach to Identity-First Security
SPHERE is a cybersecurity leader and risk-reduction innovator dedicated to helping our clients strengthen security, protect their data and accounts, and achieve ongoing Identity Hygiene. We empower security and IT teams to improve identity security and hygiene to protect their organization’s most critical assets against theft and abuse. We’ve built SPHEREboard leveraging years of industry experience to be a modern, practical platform that automates the end-to-end identity and access management process.
SPHERE’s approach to the 3 C’s:
Principle #1 – Consistent
SPHERE’s Intelligent Discovery scans all supported environments (AD, Windows, Linux, Databases, HR software, and select applications) within your organization on a consistent schedule that can be set to occur as often as you need. The ‘Intelligent Discovery’ capability provides an array of information about all identities in your environment and the accounts that they use.
After the discovery is complete, other automated procedures such as SPHERE’s Ownership Automation begin. This technology uses built-in intelligence to determine the most likely owner of an identity, account, group, or system. This leads to how SPHERE applies the principle of Context-Awareness to its platform.
Principle #2 – Context-Aware
During SPHERE’s Intelligent Discovery, important information is collected, like what each account has access to and how they are getting that access. This information is reported through what SPHERE calls, “access routes”. This provides visibility into local OS and database account access and shows which identity has access to these accounts, allowing you to see the blast radius of each account in your environment. SPHERE also classifies each account by what are referred to as, “account types”, which further contributes to helping you be more context-aware in your approach to identity security.
SPHERE also supports context-awareness by defining ownership, displaying how an account aligns with a certain part of the business, and showing which accounts are secured within a PAM vault, and which ones are not.
Principle #3 – Continuous
The built-in schedulers, campaigning, and rich automation that SPHERE has developed allow the platform to maintain a form of autonomy that enables these principles to continue functioning without the constant need for human interaction. This positions SPHERE to play a pivotal role in the identity security process chain, equipping your team with the necessary tools to adopt this new approach.
SPHERE’s software takes a holistic approach through the intersection of built-in automation and software that can support this 3 C’s approach to identity-first security. There are many approaches to identity security and cybersecurity in general, but most of the themes carry over from one to the other. At its root, Gartner’s “3 C’s” approach is no different. By focusing on providing a consistent mesh of coverage, understanding the context of the identities and assets in your environment, and then ensuring that this consistency and awareness are operationalized continuously, your organization can greatly reduce risk.